Navigating SHA: Securing Digital Life & Empowering Public Health
Table of Contents
Introduction: Unpacking the Acronym 'SHA'
When you encounter the acronym 'SHA', what immediately comes to mind? For some, perhaps a historical figure or even a specific regional context like the sha iran, evoking images of past eras. Yet, in the modern digital and public service landscape, 'SHA' takes on crucial, often unseen, roles that underpin our daily lives, ensuring both the security of our information and the well-being of communities. This article delves into the multifaceted world of SHA, exploring its vital applications in two distinct yet equally important domains: digital security through cryptographic algorithms and public welfare via health authorities.
From safeguarding sensitive data with unique digital fingerprints to providing comprehensive health coverage for millions, the impact of SHA is profound. We will explore how a Secure Hashing Algorithm (SHA) fundamentally changes data by creating unique hash digests, a cornerstone of cybersecurity. Concurrently, we will examine the Social Health Authority (SHA), a state corporation dedicated to managing public health insurance, highlighting its mission and the processes involved in accessing its services. Understanding these diverse applications of SHA is essential for navigating our increasingly interconnected world, where both digital integrity and public health infrastructure are paramount.
SHA in Digital Security: The Secure Hashing Algorithm
In the realm of cybersecurity, the acronym SHA often refers to the Secure Hashing Algorithm. This cryptographic function is a cornerstone of modern digital security, playing a critical role in verifying data integrity, authenticating digital signatures, and securing various online transactions. It's an invisible guardian, working behind the scenes to ensure that the information you send and receive remains untampered and authentic.
- Miu Shiromine
- Brandon Coleman Red Clay Strays
- Bonnie Bruise
- Exploring The World Of Roblox Condo Games A Thrilling Playground For Creativity
- Mikayla Campino Leaks
What is SHA (Hashing)?
At its core, a Secure Hashing Algorithm, or SHA, is a one-way mathematical function that takes an input (or 'plaintext message') of any size and produces a fixed-size string of characters, known as a 'hash digest' or 'hash value'. The key characteristic here is that this process is virtually irreversible. You cannot reconstruct the original data from its hash
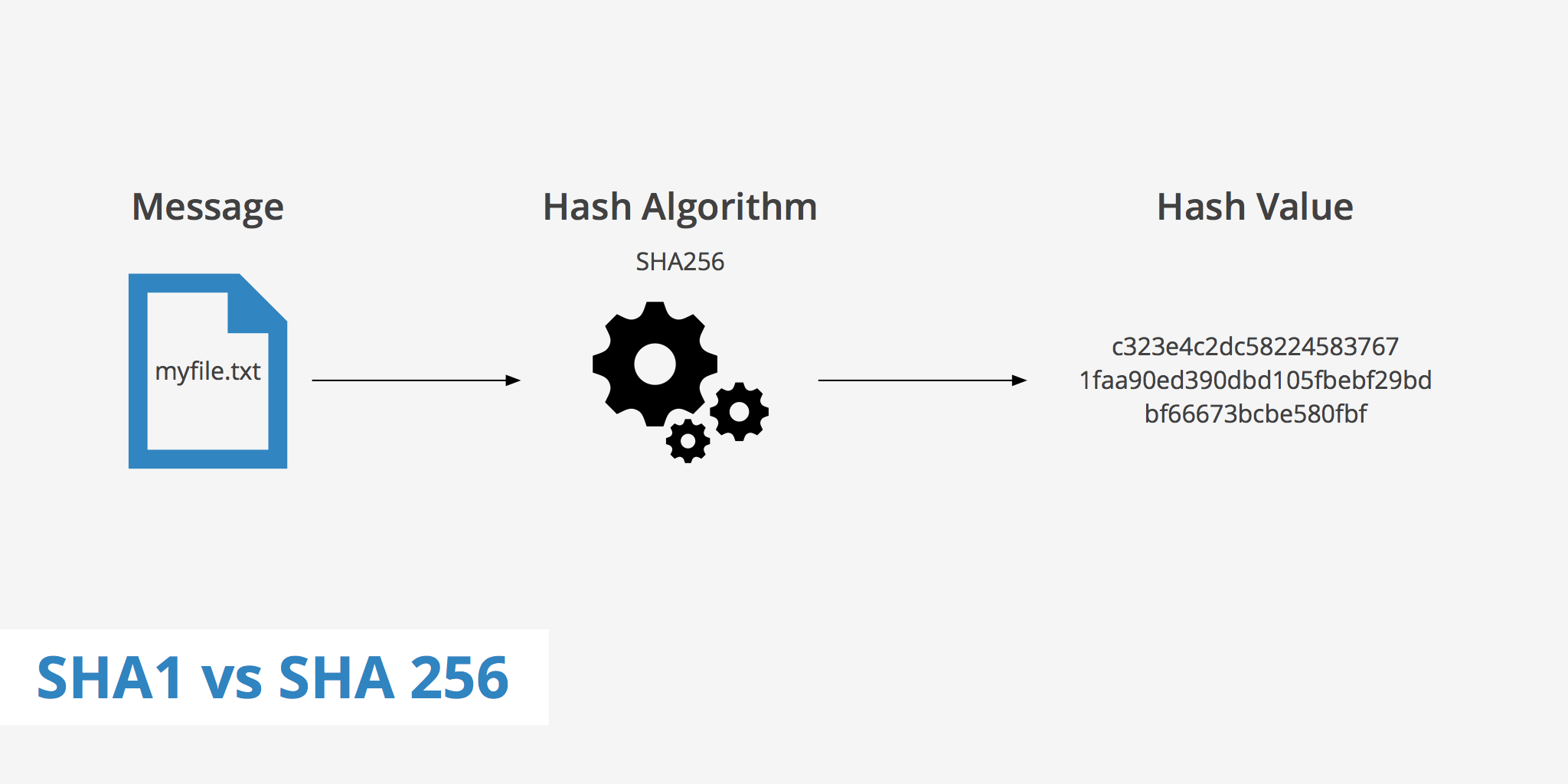
SHA1 vs SHA256 - KeyCDN Support
What is Hashing? Compare MD5, SHA1, HA2, SHA3 Hashing Algorithms
+seems+secure.jpg)
Cryptography and Network Security Chapter ppt download